Note: This section contains one or more sets of questions with the same scenario and problem. Each question presents a unique solution to the problem. You must determine whether the solution meets the stated goals. More than one solution in the set might solve the problem. It is also possible that none of the solutions in the set solve the problem.
After you answer a question in this section, you will NOT be able to return. As a result, these questions do not appear on the Review Screen.
You have a Microsoft 365 E5 subscription and use Microsoft Defender for Office 365.
You need to implement a threat policy that will apply a balanced baseline protection profile to protect against spam, phishing, and malware.
Solution: You create an anti-phishing policy.
Does this meet the goal?
Correct Answer:
B
🗳️
HOTSPOT
-
You have an on-premises server named Server1 that runs Windows Server. Server1 is used to access a software as a service (SaaS) app named App1.
You have a Microsoft 365 E5 subscription and use Microsoft Defender for Cloud Apps, Microsoft Defender XDR, Microsoft Defender for Endpoint, and Microsoft Defender for Identity. You configure Cloud Discovery for App1 and Server1.
You need to meet the following requirements:
• Tag Server1 as a high-value device.
• Ensure that an alert is triggered when App1 is accessed.
What should you do for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.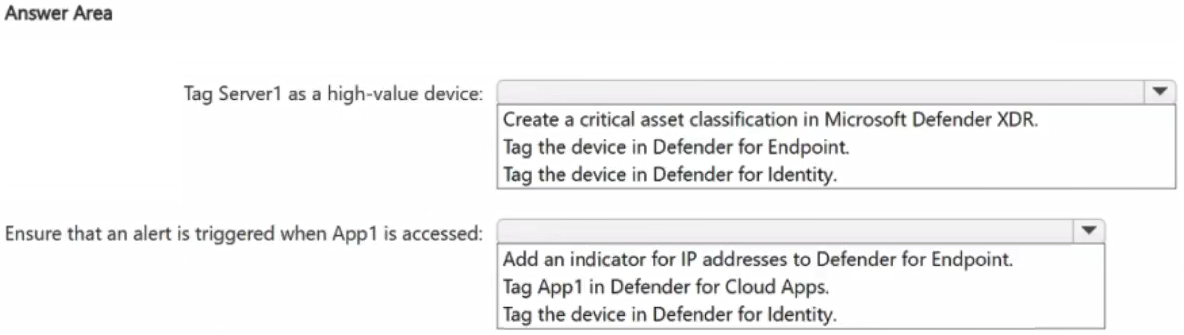
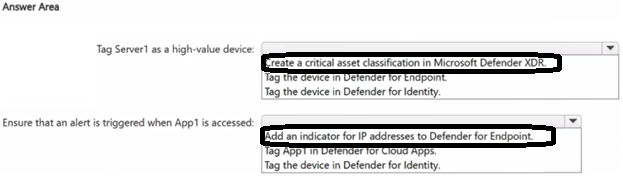
Correct Answer:
You have a Microsoft 365 E5 subscription and use Microsoft Defender for Cloud Apps.
You are reviewing the activity log of the subscription.
You need to ensure that events originating from the on-premises network are categorized automatically as Administrative.
What should you create?
Correct Answer:
C
🗳️
You have an on-premises server named Server1 that runs Windows Server.
You have a Microsoft 365 E5 subscription and use Microsoft Defender for Cloud Apps.
You plan to configure Cloud Discovery and enable automatic log upload.
You need to ensure that you can run the log collector on Server1.
What should you install on Server1?
Correct Answer:
C
🗳️
You have a Microsoft 365 E5 subscription. The subscription contains users that have Windows 11 devices.
You plan to onboard the devices to Microsoft Defender for Endpoint. The devices will connect to Defender for Endpoint through a proxy service.
You need to ensure that the devices use consolidated URLs and static IP ranges when connecting to Defender for Endpoint.
What should you do?
Correct Answer:
B
🗳️
You have a Microsoft 365 subscription that contains a Microsoft Entra tenant named contoso.com. The tenant includes a user named User1.
You plan to use Microsoft Entra ID Protection.
You need to ensure that User1 can review the list in Microsoft Entra ID Protection of users flagged for risk. The solution must use the principle of least privilege.
To which role should you add User1?
Correct Answer:
A
🗳️
You have a Microsoft 365 subscription and use Microsoft Defender for Office 365.
You need to recommend a solution to educate users on topics that relate to social engineering risks. The users must receive a weekly reminder to complete a learning task.
What should you use in the Microsoft Defender portal?
Correct Answer:
D
🗳️
You have a Microsoft 365 E5 subscription and use Microsoft Defender for Office 365.
You need to create a policy that will quarantine messages containing attachments that match .apk and .appx extensions.
Which type of policy should you configure?
Correct Answer:
A
🗳️
DRAG DROP
-
You have a Microsoft 365 E5 subscription that contains two security groups named Group1 and Group2.
You need to recommend an authentication solution to meet the following requirements:
• Administrators must be able to generate a time-limited code to allow the members of Group1 to authenticate without using their password.
• The members of Group2 must be able to authenticate by confirming a two-digit code on their mobile device.
Which authentication method should you recommend for each group? To answer, drag the appropriate methods to the correct groups. Each method may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.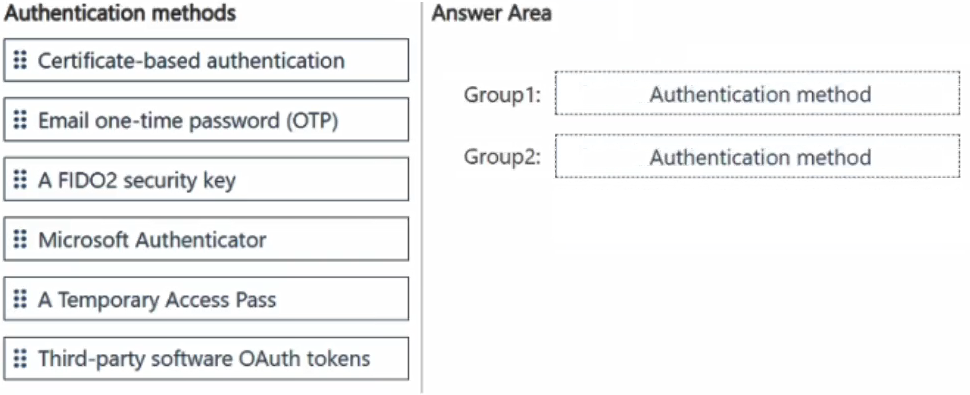
Correct Answer:

HOTSPOT
-
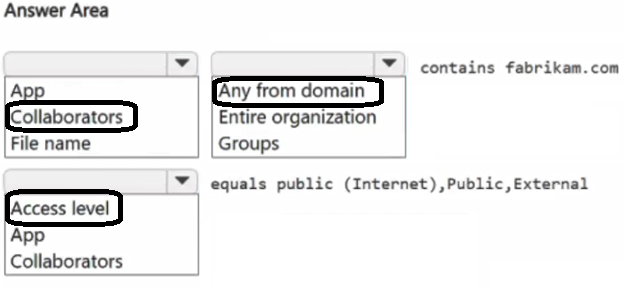
You have a Microsoft 365 E5 subscription and use Microsoft Defender for Cloud Apps.
You need to create a file policy to generate an alert when a file is shared with a domain named fabrikam.com.
How should you complete the filter for the policy? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.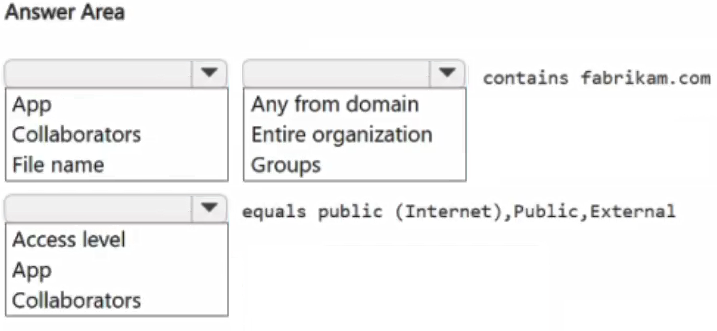
Correct Answer: