You have a Microsoft 365 subscription that includes Microsoft Intune and Microsoft Defender XDR.
All users have devices that run Windows 11.
From the Microsoft Defender portal, you review the Microsoft Secure Score recommendations. One of the top recommendations is to block all Microsoft Office applications from creating child processes.
You need to increase the secure score by addressing the recommendation.
What should you do?
Correct Answer:
D
🗳️
You have a Microsoft 365 E5 subscription and use Microsoft Defender for Office 365.
You need to implement a social engineering awareness solution that meets the following requirements:
• To reset a user's password, emulate an email message that contains a link.
• Track any users that selects the email message link.
• Suggest further social engineering training.
What should you use in the Microsoft Defender portal?
Correct Answer:
C
🗳️
You have a Microsoft 365 E5 subscription and use Microsoft Defender for Office 365.
You are configuring Attack simulation training that will target all users and use the Credential Harvest social engineering technique.
You need to ensure that the simulation sends an email message that contains a custom phishing link and company-based terminology and branding.
How should you configure the simulation?
Correct Answer:
A
🗳️
HOTSPOT
-
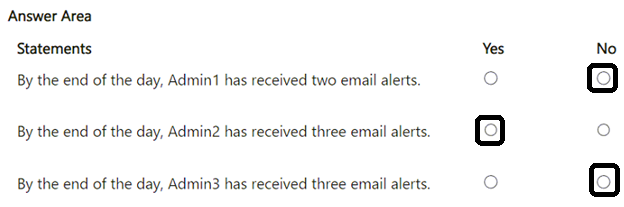
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.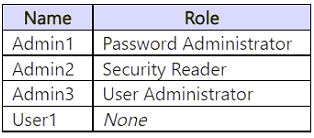
You use Microsoft Entra ID Protection.
For the Users at risk detected alerts setting, you configure the following:
• Recipient: Admin1
• Alert on user risk level at or above: Medium
User1 signs in to Microsoft 365 services and is assigned the detected risk levels shown in the following table.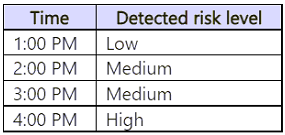
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.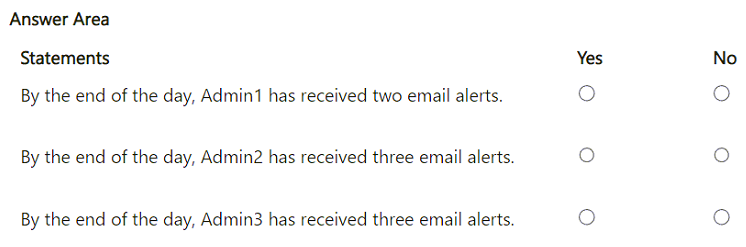
Correct Answer:
You have a Microsoft 365 E5 subscription that contains Windows 11 devices.
All the devices are onboarded to Microsoft Defender for Endpoint.
You need to compare the configuration of the devices against industry standard benchmarks.
What should you use?
Correct Answer:
C
🗳️
You have a Microsoft 365 E5 subscription and use Microsoft Defender for Endpoint.
Defender for Endpoint has tamper protection enabled.
You have a device named Device1 that is onboarded to Defender for Endpoint.
You need to configure antivirus and real-time protection for Device1.
What should you do in the Microsoft Defender portal?
Correct Answer:
C
🗳️
You have a Microsoft 365 E5 subscription.
You plan to configure Privileged Identity Management (PIM) for the User Administrator role in Microsoft Entra.
You need to ensure that a user can make a role assignment request for the User Administrator role only during the next six months.
How should you configure the assignment?
Correct Answer:
A
🗳️
DRAG DROP
-
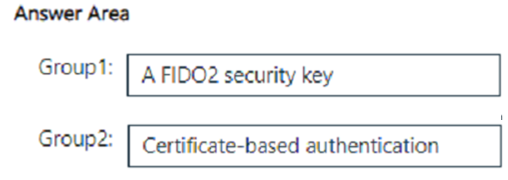
You have a Microsoft 365 E5 subscription that contains two security groups named Group1 and Group2.
You need to recommend an authentication solution that meets the following requirements:
• Members of Group1 must be able to authenticate by using a hardware token.
• Members of Group2 must be able to authenticate by using a public key infrastructure (PKI).
Which authentication method should you recommend for each group? To answer, drag the appropriate methods to the correct groups. Each method may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.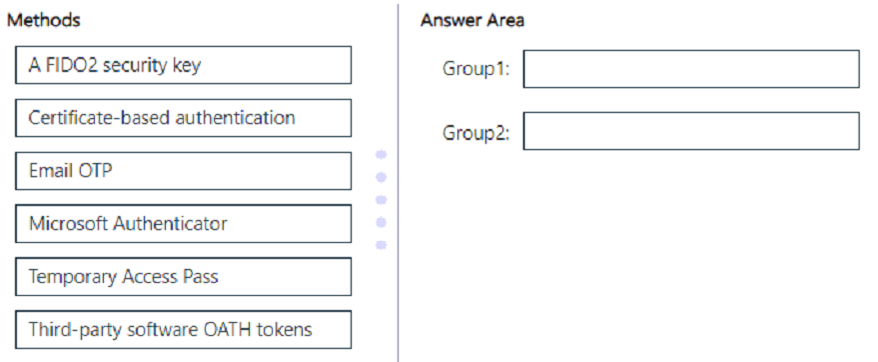
Correct Answer:
HOTSPOT
-
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.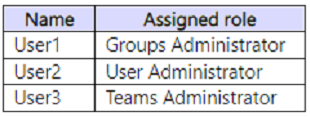
Which users can create user objects, and which users can create Microsoft 365 groups? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.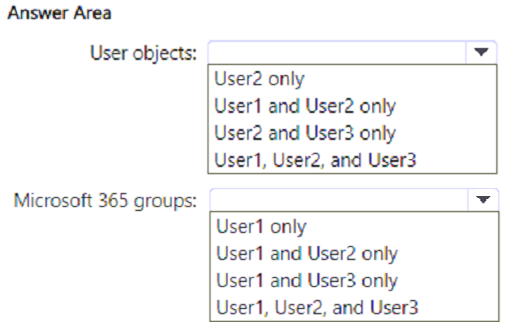
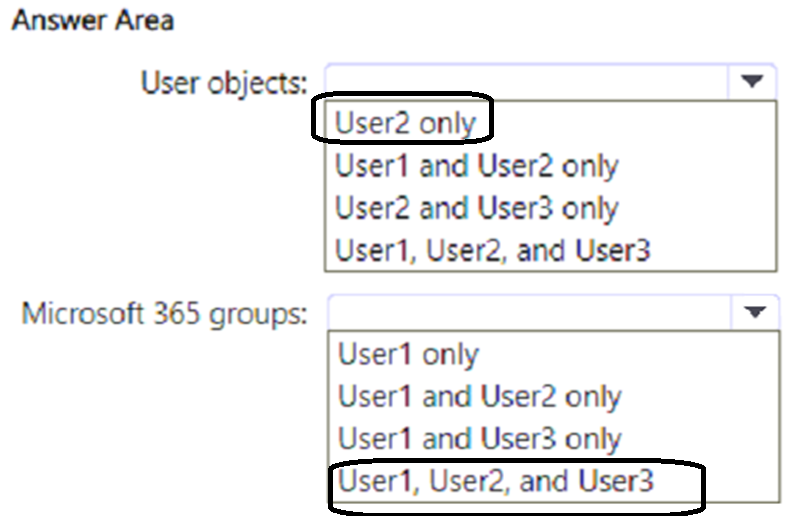
Correct Answer:
HOTSPOT
-
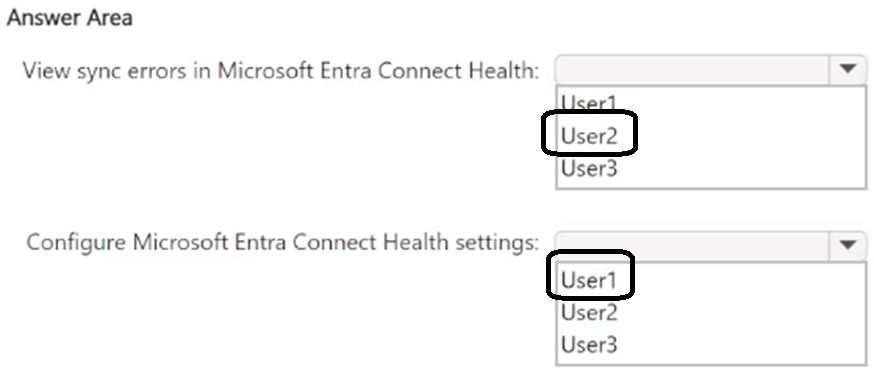
You have a hybrid deployment of Microsoft Entra that contains the users shown in the following table.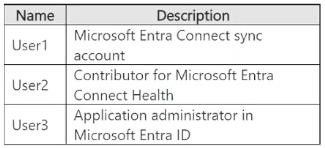
You need to identify which users can perform the following tasks:
• View sync errors in Microsoft Entra Connect Health.
• Configure Microsoft Entra Connect Health settings.
Which user should you identify for each task? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.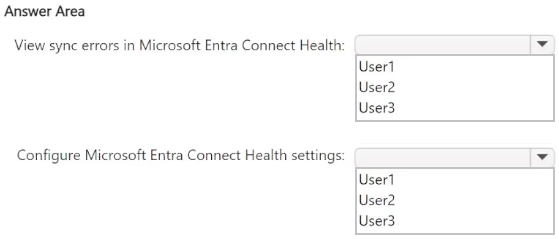
Correct Answer: